Deploying Cloud NGFW using Terraform
This is a multi-section tutorial, with dependencies between each section. Please perform each section in order, per the links on the left-hand sidebar.
Objective
The objective of this multi-section tutorial is to deploy Cloud NGFW into AWS with Terraform. The sections are divided as follows:
- This introduction
- Prepare AWS infrastructure
- Subscribe to and prepare Cloud NGFW
- Create a Cloud NFGW rulestack and rules
- Commit the Cloud NFGW rulestack and rules
- Create Cloud NFGW resources
- Create routing to insert Cloud NGFW into the infrastructure
- Testing, log inspection and review
The entire source code for this tutorial can be found on GitHub.
Introduction
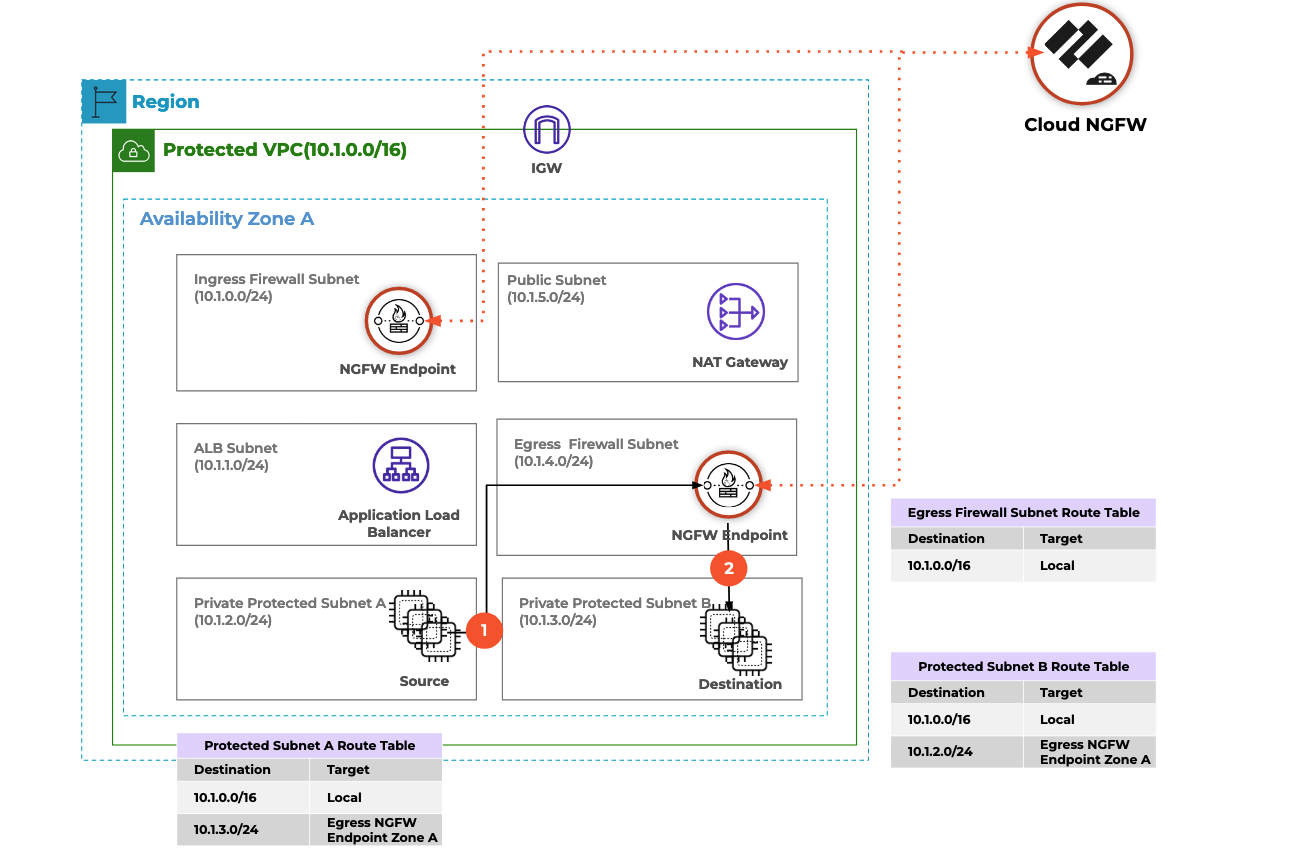
There are many ways to architect Cloud NGFW into your AWS infrastructure. This tutorial uses one of the reference architecture designs from Palo Alto Networks, described in the "Protect Traffic between TWO subnets in a VPC" section and shown in Figure 6. Using this design pattern, you will deploy Cloud NGFW into a single VPC in a single availability zone, and protect traffic between two hosts deployed into two separate DMZ subnets. The endpoints used to steer traffic into Cloud NGFW Will be service-managed.
This tutorial follows the convention of splitting up Terraform code into separate files, namely:
providers.tf- definition and configuration of Terraform providers to be usedvariables.tf- declaration of variables which will be usedterraform.tfvars- when required, defines values for variablesmain.tf- definition and creation of resources (for example, AWS infrastructure, Cloud NGFW rules, etc)outputs.tf- declaration of values to be presented back after Terraform finishes executing
The content in this tutorial builds on the introduction published in Palo Alto Networks' Developer Blog.
Assumptions
This tutorial/guide assumes:
- a working installation of Terraform
- working connectivity to AWS
- credentials for an AWS user capable of performing operations with your AWS account such as creating, listing, updating and deleting resources such as VPCs, subnets, route tables and routes, IAM roles
Important - Work in a Lab Environment First
With all of the tutorials and guides presented on this website, please ensure that you attempt the tasks in a lab or a similar safe and non-production environment first. In public cloud scenarios, this should be a non-production cloud account which contains no production assets or data. Confirm the tasks behave as expected and perform the operations you require, before using them in production or other live environments.